
Today is the final day before officially clock in for the first time as an IT professional. I messed around with serviceNOW earlier this week and just today completed a free course that included getting my hands dirty with active directory. I am happy to have gotten some exposure to some of the tools I will be using on the job before starting training. I know, I know… you get most of the experience on the clock. This will be my first job in the IT field so I figure nobody will be mad at me (especially the trainer) for being able to pick things up a little quicker since I’ve already been exposed to the software.
I have been taking courses on TCM academy and boy oh boy, have I enjoyed all of it! This is a company started by Heath Adams (aka the cyber mentor) to teach people about ethical hacking and penetration testing. The guy also does consulting and penetration testing and he knows his stuff. I really enjoy the video/lab format they offer on their website, and they even have free courses (like this one) for you to see if their format works for you! I’m sure most of you have heard of the hands on learning platforms like HackTheBox and TryHackMe (just to name a few popular ones). These platforms are highly revered for their hands on approach to learning, and TCM aims to provide a hands on experience with their practical certifications. I’m not talking about capture the flag. I’m talking about certifications where you actual have to run a for real penetration test with rules of engagement and a statement of work and write a full report on everything you did and everything you discovered. Some highly regarded certs by HR (like the EC council’s CEH, please don’t yell at me) have a bad reputation amongst cyber security professionals for being a horridly overpriced multiple choice exams, and when it comes to cyber security, I have learned that experience is king. HR might want certs, you might actually need some to pass a few filters, but the security people hiring you want you to actually know stuff. I am not sponsored or anything but the TCM platform focuses on showing you step by step videos + running through virtual machines and doing things yourself. Check them out if you’re interested. They also put up youtube videos, but that’s the end of my spiel, let’s talk about the lab.
To start things off, I have a pretty decent PC. I originally intended for it to just be a gaming computer, but as I’ve gravitated towards the realm of cyber security I have made some serious upgrades that I am now cashing in on. https://pcpartpicker.com/user/PoBoyTech/saved/hYRzZL
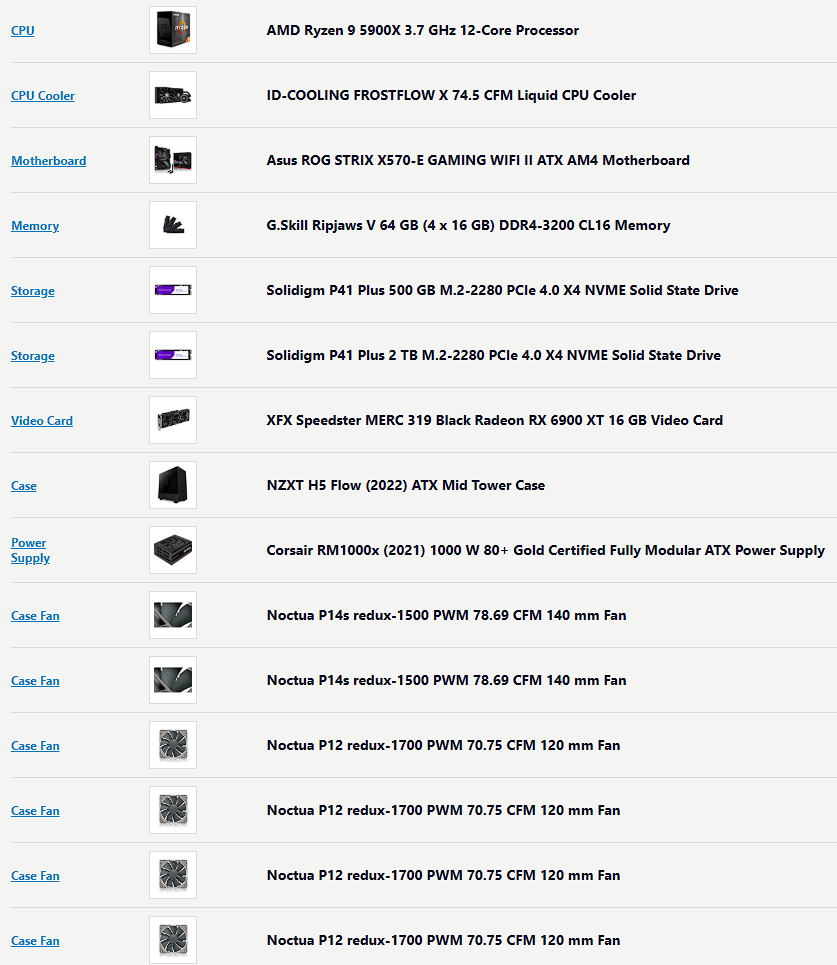
As you can see, my rig is more than capable of pulling off some decent virtualization, and I definitely enjoyed a smoother lab experience because of it. For the AD lab I had to run a windows 11 pro machine and a windows 2022 server machine as a domain controller, to each I allocated 8GB ram, 4 cores, and 50GB storage( you can lower specs/leave default if you have lower end hardware). I skipped the unattended installation on both, as I had some settings to tweak. I would like to remind everyone to always run the Guest Additions Setup (VirtualBox) as it will allow for a better virtualization experience with improved resolution, window resizing, etc.
Devices > Insert Guest Additions CD Image > Defaults > Finish & Reboot Now.

At this point I used the built in snap shot feature to back up the current state of my virtual machine, a habit that I strongly implore all aspiring pc techs to adopt, and gave it the traditional name of Fresh <OS Version> Install. For my next task I gave the machine the server role of Active Directory Doman Services, promoted the server to a domain controller, gave it the root domain name LAB.local, created the Directory Services Restore Mode (DSRM) password, and accepted a bunch of default settings until I got to a LAB\administrator login. Success!
I then added the Active Directory Certificate Services, this allows me to use secure versions of protocols for server communication, like authentication etc. I created the enterprise CA(certificate authority), root CA, and a new private key (RSA#MSSKP 2049 w SHA256) w/ a validity of 5 years.


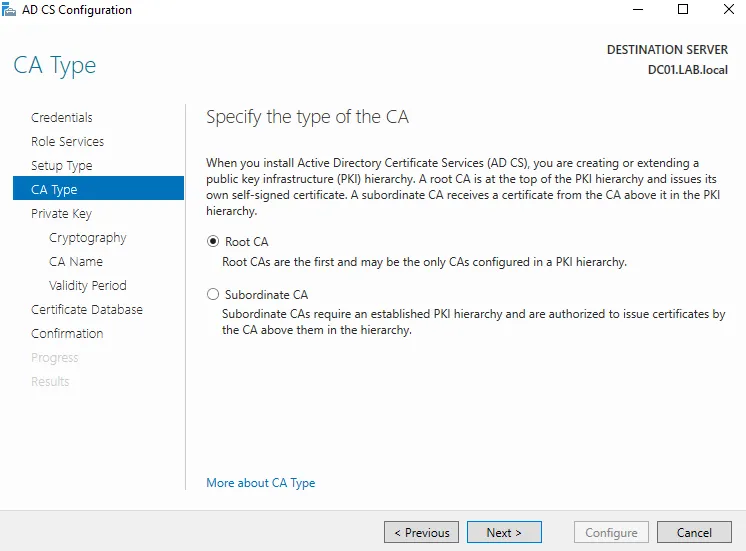


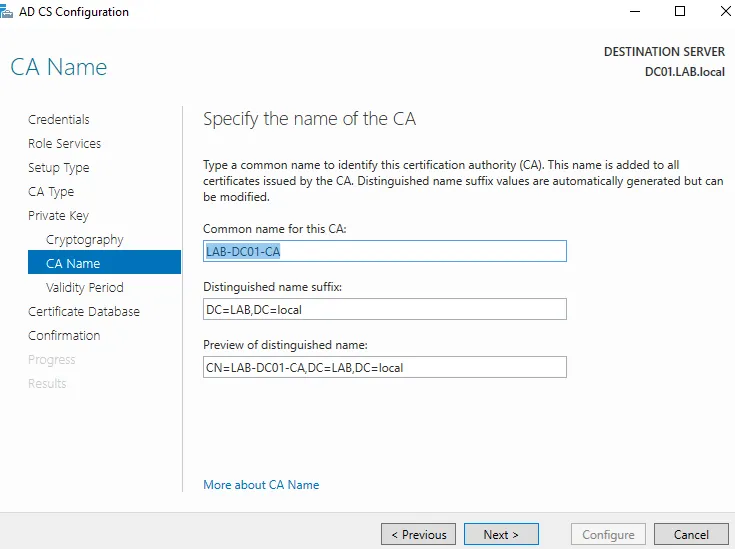

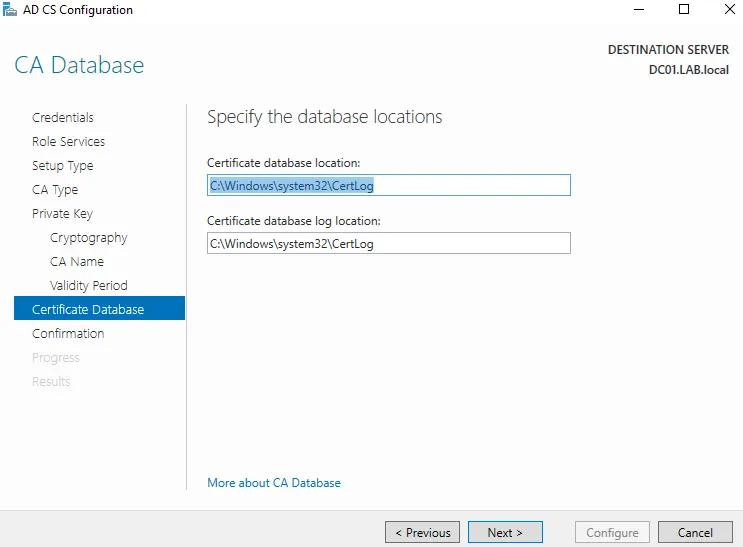
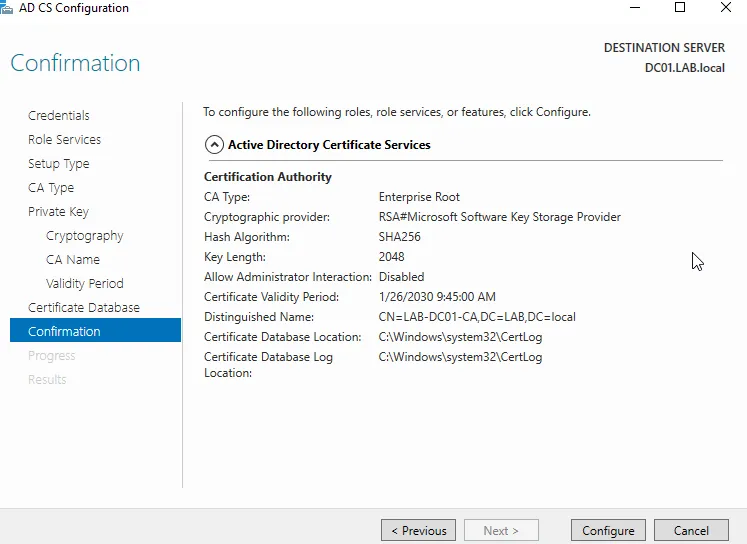
At this point I went into the VirtualBox network manager and added the W11pro/WS22 vm’s to a nat network, gave them static IP addresses, set the WS22 vm dns to loopback (since it is hosting dns), and set the W11pro vm dns to the ip address of the WS22 vm. I then used the work/school settings on the W11 vm to connect and join it to my local AD domain: LAB.local via the domain admin account and rebooted the system.
Next I created a new OU: Groups and dragged all the pre populated groups from the users container into the new OU.


This is better for security as containers cannot actually have group policy objects(GPO) directly applied to them, rather you would use Organizational Units(OU) to do this. I created several “department” OU’s and then created a user and copied new ones into each department OU. I’m not a pro or anything but it definitely made sense to me. Basically GPO’s allow more granular access controls and they are one of the major reasons for active directory being so popular and widely used.
I then created a network share (smb share quick): \\DC01\EngineeringShare, disabled inheritance, and removed the domain users that would allow anyone access to the share. I then mapped the network drive onto one of the user accounts for easy access. I uploaded a custom background image to the netlogon share and then added a GPO to the engineering OU to set any engineering users backgrounds to the custom background (User Config > Policies > Administrative Templates > Desktop > Desktop > Desktop Wallpaper > Enabled > custom image path). I then created new GPO to restrict the engineering users from changing their desktop wallpaper.

I have worked through a decent chunk of the above book, so the next part of the labs on using powershell wasn’t too difficult to grasp. Basically I logged back into the W11 machine as the domain admin and then created a script to create a new AD user.
#Script to create a new AD user with the parameters passed in by the user
#Getting parameters for script from user
param (
[Parameter(Mandatory=$true)]
[string]$FirstName,
[Parameter(Mandatory=$true)]
[string]$LastName,
[Parameter(Mandatory=$true)]
[string]$UserName,
[Parameter(Mandatory=$true)]
[string]$OU,
[Parameter(Mandatory=$true)]
[string]$Domain
)
#Generate Random Password
$Password = -join((0x30..0x39)+(0x41..0x5A)+(0x61..0x7A) | Get-Random -Count 12 | ForEach-Object {[char]$_})
Write-Host "Password Generated as: $Password"
$SecurePassword = ($Password | ConvertTo-SecureString -AsPlainText -Force)
#Make a call to New-ADUser to create the AD user
New-ADUser `-SamAccountName $UserName`
-UserPrincipalName "$Username@$Domain" `-Name "$FirstName $LastName"`
-GivenName $FirstName `-Surname $LastName`
-AccountPassword $SecurePassword `-Enabled $true`
-Path "OU = $OU, DC = LAB, DC = local" `-PasswordNeverExpires $false`
-ChangePasswordAtLogon $true
After all that I ended up created another GPO: AccountLockoutPolicy for the entire domain (Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Account Lockout Policy > Account Lockout Threshold > Define Policy: 3 > Apply) and enforced it. I tested the lockout by failing multiple login attempts on an AD user and it worked! I then used powershell to unlock the account, reset the password, set the user to change their password at next logon, and verify that these settings were changed.
Set-ADAccountPassword -Identity bbob -reset
Set-ADuser -Identity bbob -ChangePasswordAtLogon $true
Get-ADUSer bbob -Properties *
So, here I am, closing out my studies for the night. I know I will be getting more experience working with ticketing systems and active directory on my new job but I really wanted to do everything I could to prepare myself for it before the first day. I close this blog out by saying thanks to TCM Academy for the great learning material.
Tomorrow I am a Help Desk Technician II. I finally made it happen. I finally made it into IT. Next stop, cyber security!


Leave a Reply